System Administration - Changing LDAP Expiry and Lockout Times
Oracle single sign-on (LDAP) counts how many times a user tries to login with a bad password. This count is not per session, it is cumulative. Therefore, a user may type a bad password once on Monday, then again on Thursday, and once again on Friday, then on Friday they will get the message that the account is locked. This is confusing to the user as users do not remember that they typed their password wrong on Monday. There are settings that can be changed to alleviate this problem.
There are also settings that allow the administrator to change the default expiry times set for all LDAP passwords.
Navigate to the ODSM screen shown below and find the “cn=default” for your domain.
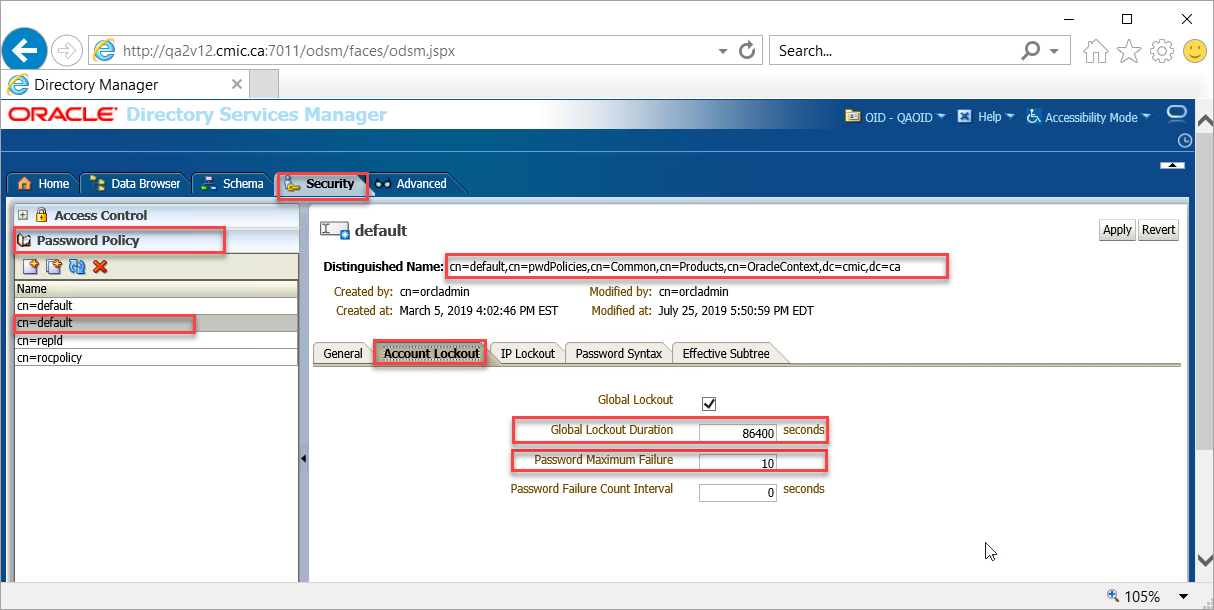
The Global Lockout Duration field set to “86400” seconds means that if a user is locked, after 86400 seconds (24 hours), it will be unlocked automatically.
The Password Maximum Failure field set to “10” means that if a user tries a wrong password 10 times, that user account will be locked.