Overview
After a Collaboration Administrator publishes a project to Project Gateway, collaborators are invited to join the project team. When an external collaborator is invited to join the project, they will receive an email where they will be asked to complete their enrollment to access the CMiC Collaborate system.
To help guide collaborators through the enrollment process after the Azure security transition, step-by-step examples of each of the various options used to register and log into the system are provided below.
NOTE: Group email addresses are not supported. This is a technical limitation of Microsoft. Each user must log in using their individual email account.
NOTE: Collaborators are not required to use a Microsoft account but will be prompted to log in through the Microsoft Login page. From this page, users can log in using other providers such as Google, Yahoo, AOL, or Protonmail, even though the Login page is branded as Microsoft. Users will be prompted to use their email address and the password associated with that email provider, not their previous CMiC Gateway password, to log into Gateway through Azure.
Microsoft Outlook Collaborate Gateway Registration
When registering using Microsoft Outlook, there are two options available for multifactor authentication:
-
Alternate Email Address
-
Alternate Phone Number
The registration process for each of these options is described below.
Alternate Email Address
This is the process flow users can expect when using an alternate email address as a form of multifactor authentication.
-
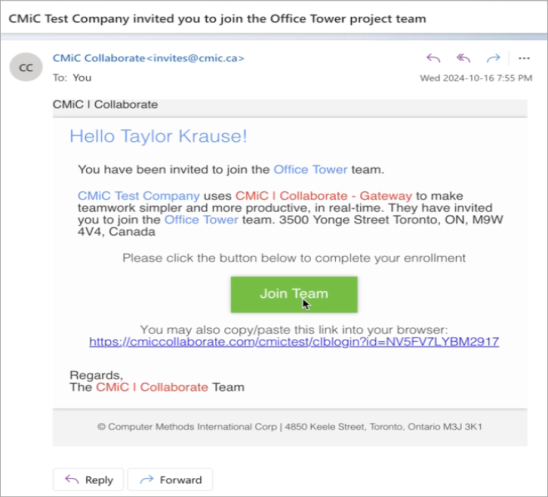
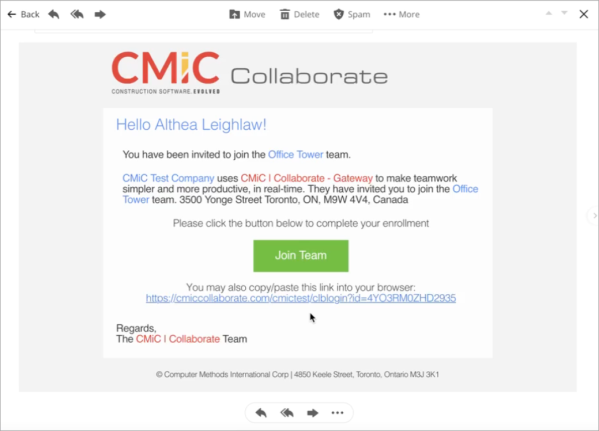
In the invitation email, click on the [Join Team] button or copy the link into (ideally) private browsing to continue the registration process.
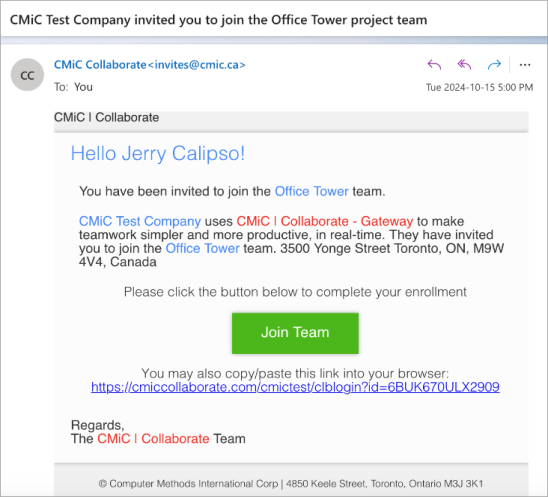
-
You will be directed to the Microsoft Login page. Sign into your account.
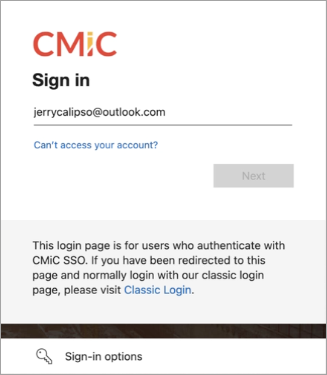
-
You must accept permissions to continue the registration process.
NOTE: CMiC does not gain access to users’ mailboxes, OneDrive, Teams, or any personal or sensitive content. This is standard Microsoft B2B OAuth behavior, and access is strictly limited to what’s necessary for authentication and authorization. To learn more, refer to Data Handling for External Collaborators.

-
You will be prompted to set up a form of multifactor authentication. In this example, we are using an alternate email address. Enter an alternate email address and press [Next].
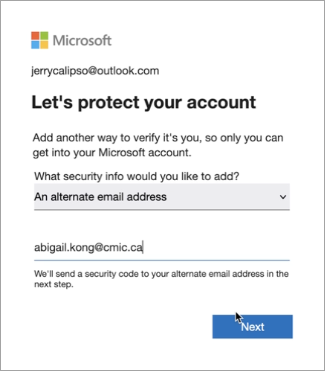
-
You will receive a Microsoft account security code. In this example, the security code has been sent to the alternate email address specified in the previous step.
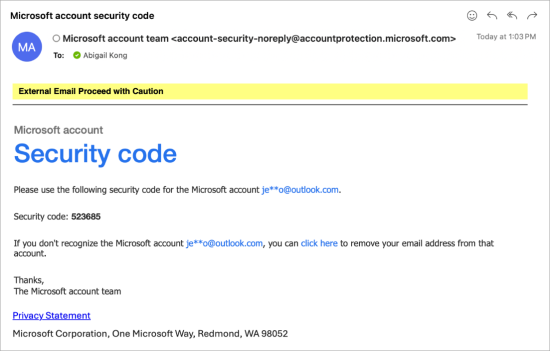
-
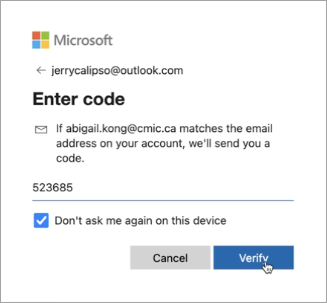
Enter the Microsoft account security code and press [Verify].
-
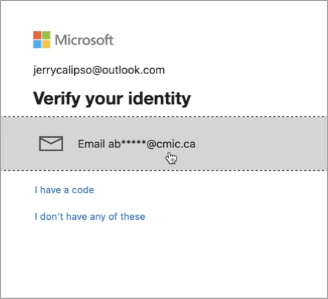
Verify your identity using the alternate email address.
-
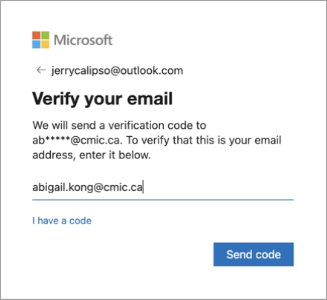
Verify your alternate email address and press [Send code].
-
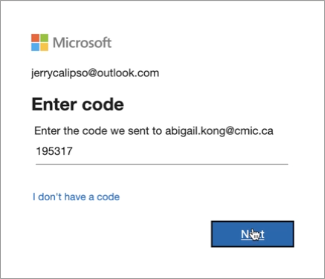
Enter the Microsoft account security code sent to your alternate email address and press [Next].
-
Once multifactor authentication is set up and verified, you will be taken to the project dashboard.
Alternate Phone Number
This is the process flow users can expect when using an alternate phone number as a form of multifactor authentication.
-
In the invitation email, click on the [Join Team] button or copy the link into (ideally) private browsing to continue the registration process.
-
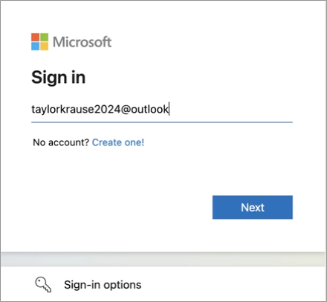
You will be directed to the Microsoft Login page. Sign into your account and press [Next].
-
You must accept permissions to continue the registration process.
NOTE: CMiC does not gain access to users’ mailboxes, OneDrive, Teams, or any personal or sensitive content. This is standard Microsoft B2B OAuth behavior, and access is strictly limited to what’s necessary for authentication and authorization. To learn more, refer to Data Handling for External Collaborators.

-
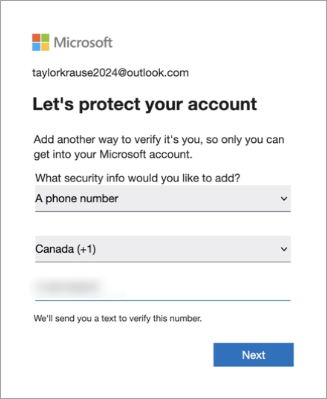
You will be prompted to set up a form of multifactor authentication. In this example, we are using a phone number. Enter the phone number and press [Next].
-
You will receive a Microsoft account security code. In this example, the security code has been sent by text message to the phone number specified in the previous step.
-
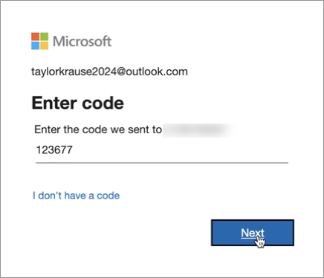
Enter the Microsoft account security code and press [Next].
-
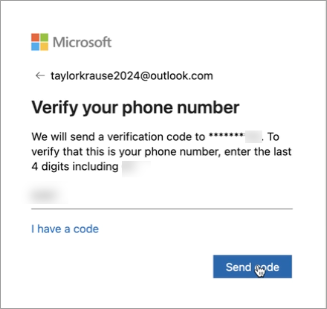
Verify your phone number to confirm your identity and press [Send code].
-
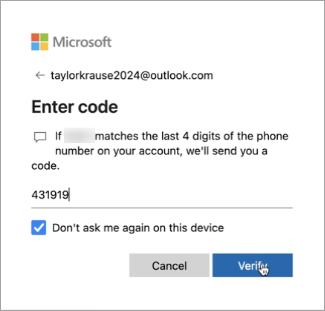
Enter the Microsoft account security code sent to your phone number and press [Verify].
-
Once multifactor authentication is set up and verified, you will be taken to the project dashboard.

Data Handling for External Collaborators
When users see a Microsoft prompt requesting permission to access their profile data, it’s part of Microsoft Entra ID (formerly Azure AD) B2B collaboration. This prompt appears because the user is being added as a guest in CMiC’s Entra ID tenant to securely access a shared application via OAuth.
To clarify:
-
No privileged or sensitive data (e.g., emails, documents, passwords, or full directory access) is shared with CMiC.
-
The permissions shown include:
-
Receive your profile data – This refers to basic directory information (e.g., name, email, tenant ID) that is required to authenticate and identify the user within the application.
-
Collect and log activity data – This refers only to access logs (e.g., sign-ins, usage) for auditing and security purposes. It does not include content or communications.
-
Use your profile data and activity data – This is solely for identifying users within the application and tracking their access to the app for compliance.
-
We do not receive access to any users’ mailboxes, OneDrive, Teams, or any personal or sensitive data. Rest assured that this is standard Microsoft B2B OAuth behavior and that access is restricted to only what’s needed to authenticate and authorize the user.
Mobile Microsoft Outlook Collaborate Gateway Login
This is the process flow users can expect when logging in using mobile with Microsoft Outlook.
-
Launch the Construct PM app and tap the [Sign in with Microsoft] button. Sign into your account using your email address and tap [Next]. You will need to verify your identity using multifactor authentication. In this example, we are using an alternate email address as a form of multifactor authentication. Verify your alternate email address and tap [Send code].
NOTE: Refer to Microsoft Outlook Collaborate Gateway Registration above for more information on setting up multifactor authentication options.
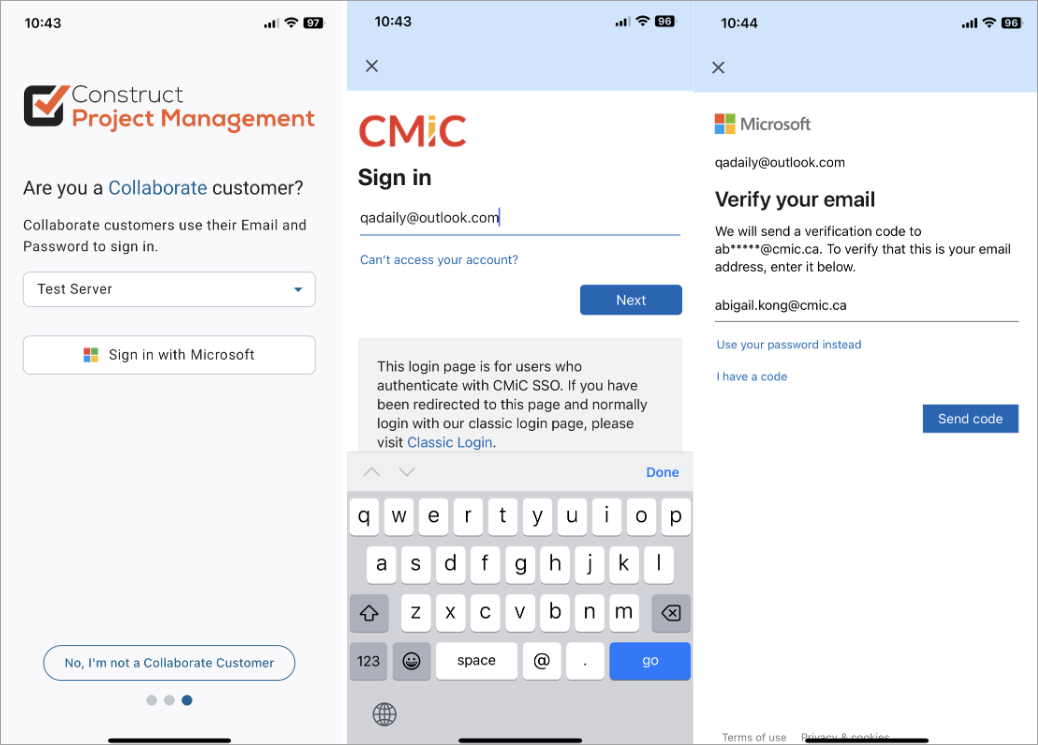
-
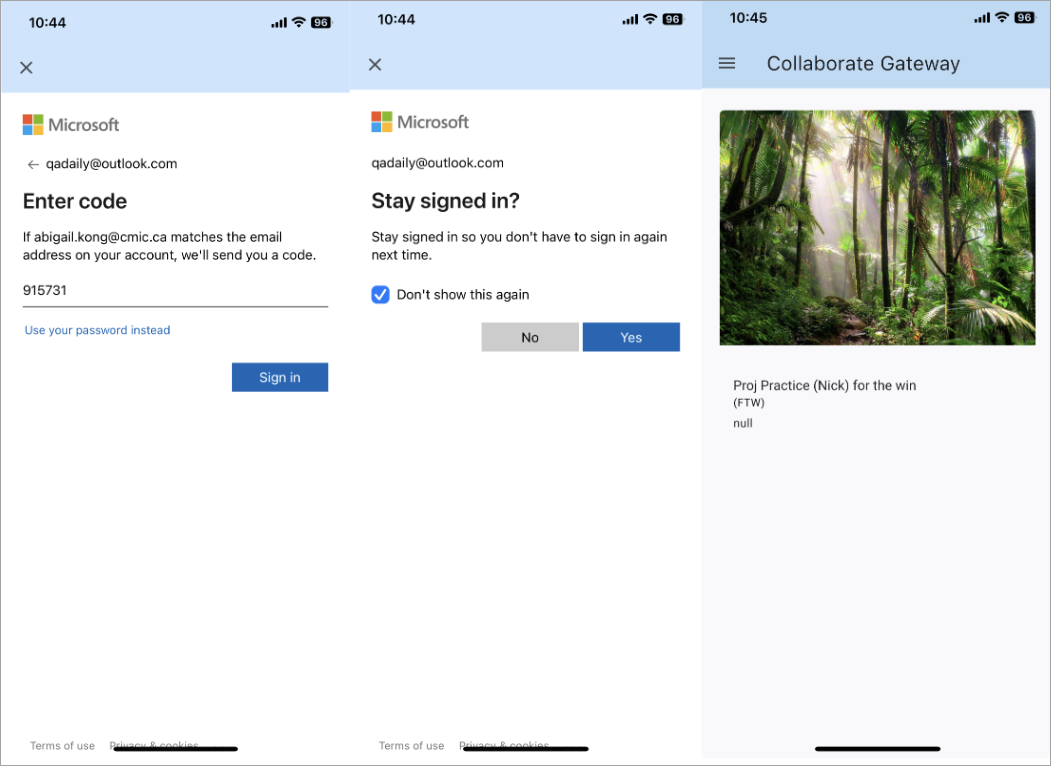
Enter the Microsoft account security code sent to your alternate email address and tap [Sign in]. Check the 'Don't show this again' box to stay signed in, so you don't have to sign in again next time. Tap [Yes] to proceed to Collaborate Gateway.
Gmail Collaborate Gateway Registration
This is the process flow users can expect when registering using Gmail.
-
In the invitation email, click on the [Join Team] button or copy the link into (ideally) private browsing to continue the registration process.
-
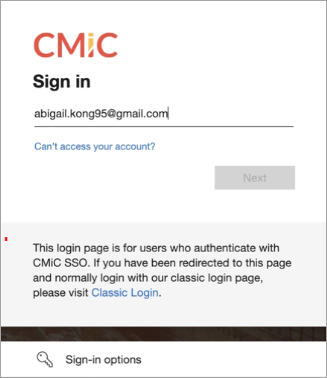
You will be directed to the Microsoft Login page. Sign into your account.
-
You will be redirected to Google to sign in.

-
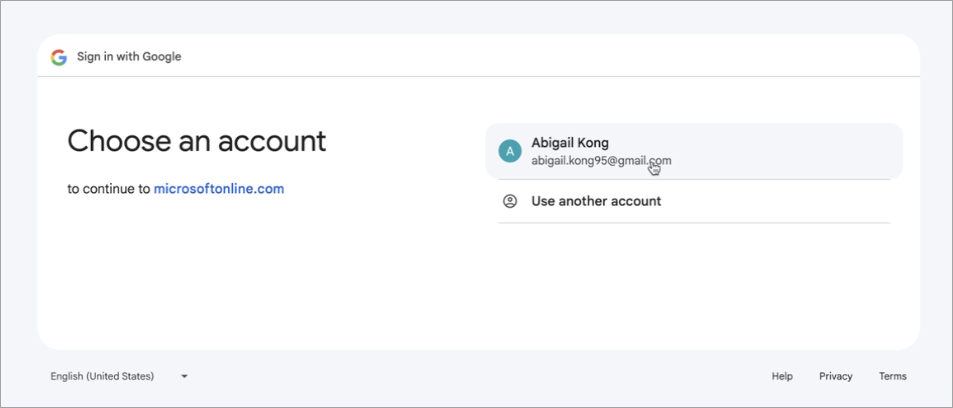
You will be prompted to choose your Gmail account to set up multifactor authentication.
-
After choosing your Gmail account, press [Continue] to proceed.
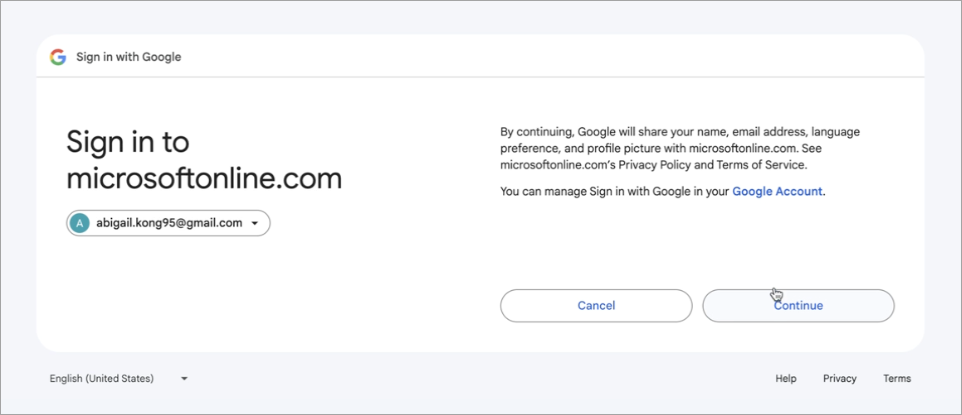
-
You will be prompted to set up multifactor authentication. Press [Next] to continue.
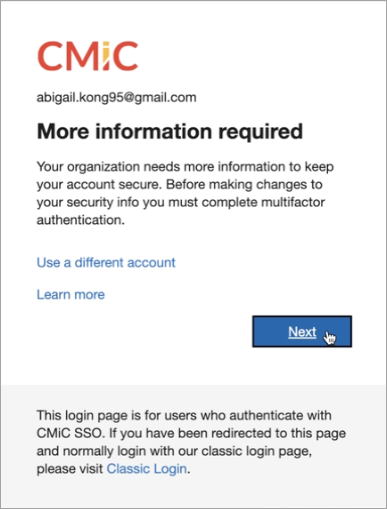
-
Install the Microsoft Authenticator app on your phone. Once the app is installed, press [Next].
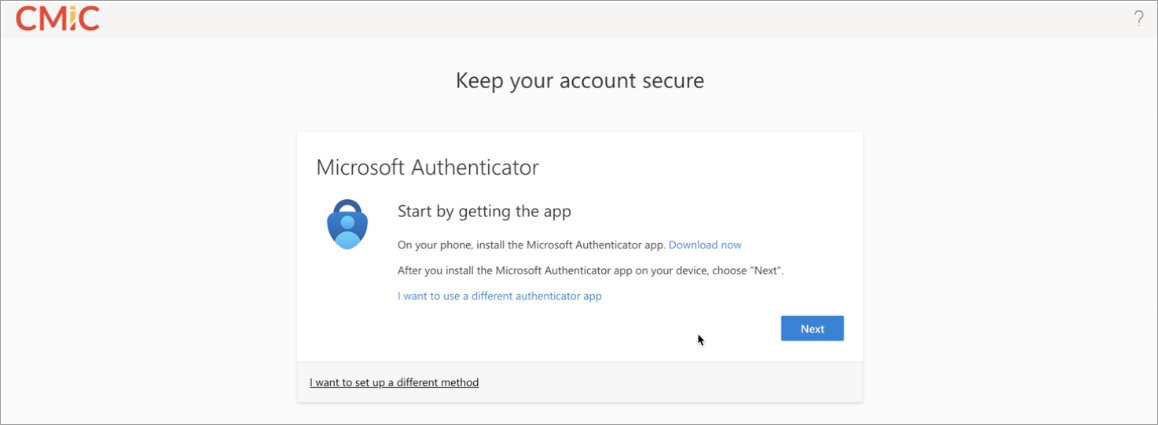
-
Continue setting up your account and press [Next].
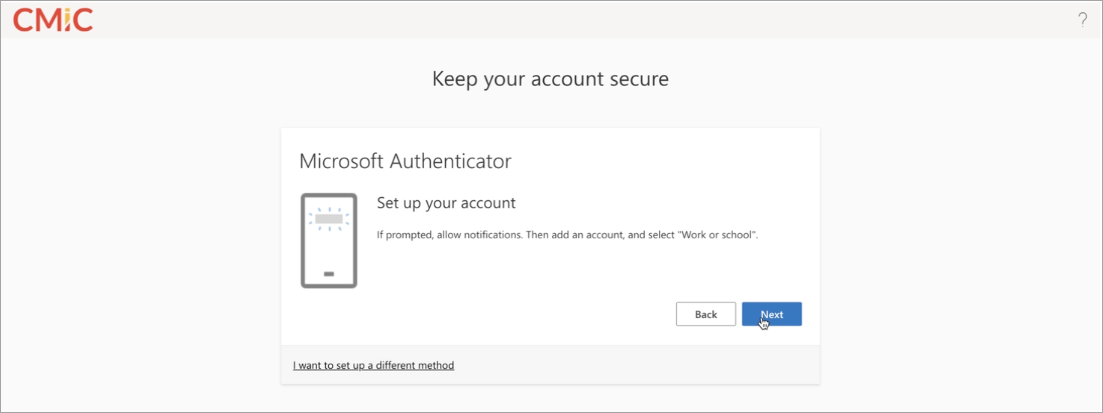
-
Use the Microsoft Authenticator app to scan the QR code. This will connect the Microsoft Authenticator app with your account. After you scan the QR code, press [Next].
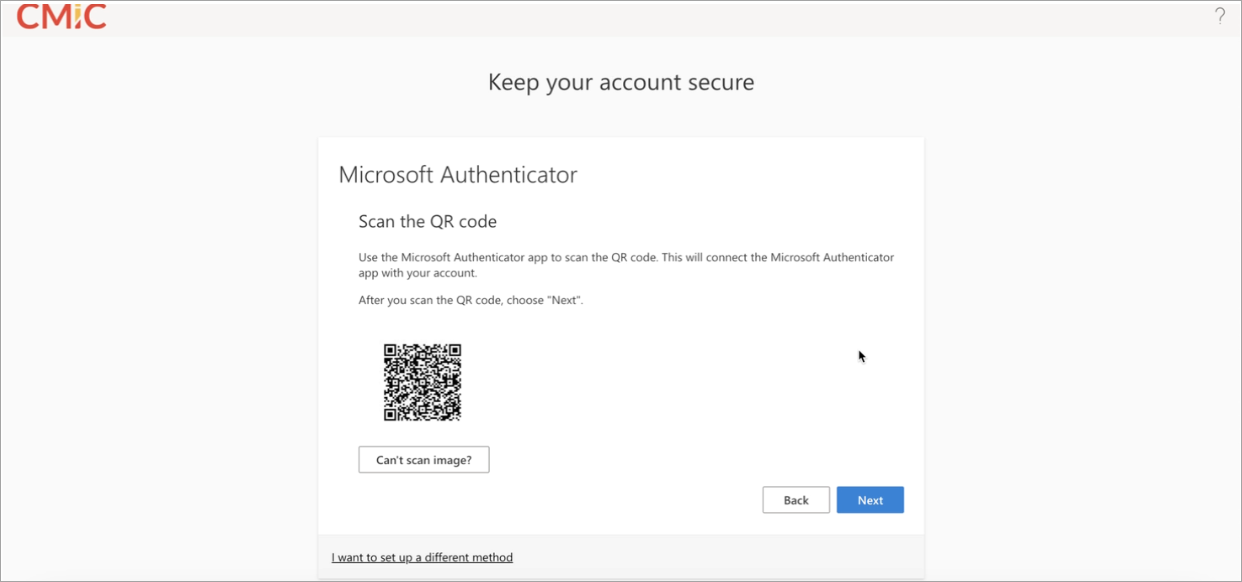
-
Approve the notification being sent to your app by entering the number provided.
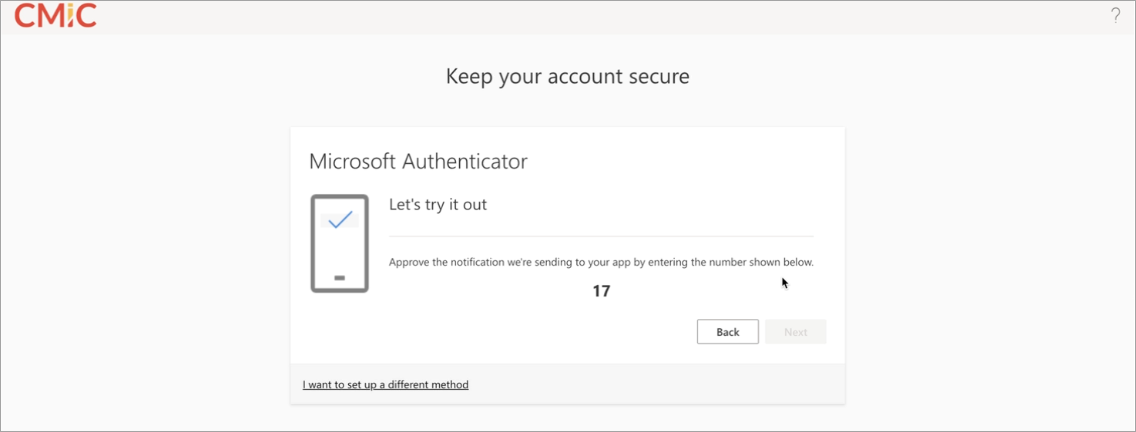
-
Once your Microsoft Authenticator app is successfully registered, press [Done].
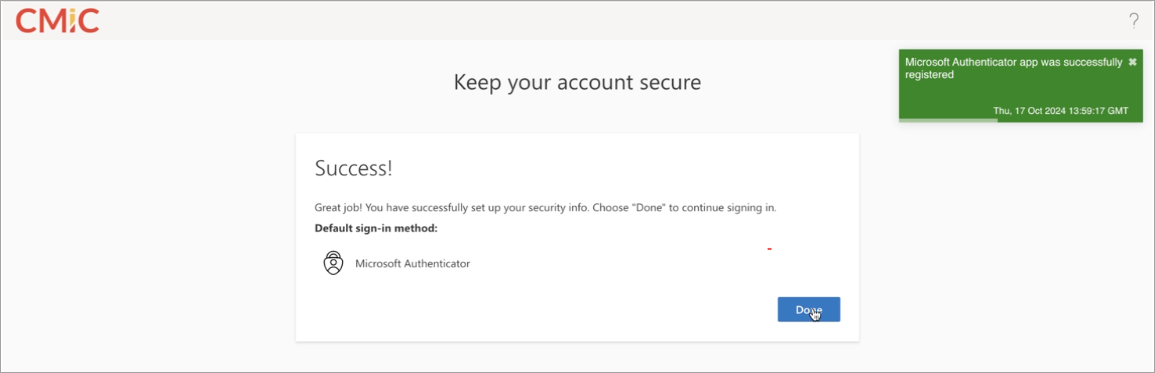
-
Once multifactor authentication has been set up and verified, you will be taken to the project dashboard.
Mobile Collaborate Gateway Google Login
This is the process flow users can expect when logging in using mobile with Google.
-
Launch the Construct PM app and tap the [Sign in with Microsoft] button. You will be prompted with a pop-up where you should choose [Continue] to proceed with signing in.
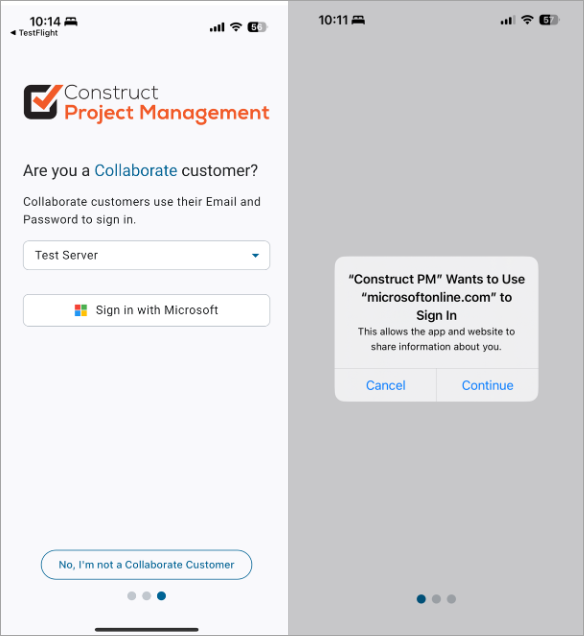
-
You will be directed to the Microsoft Login page. Sign into your account and click [Next].
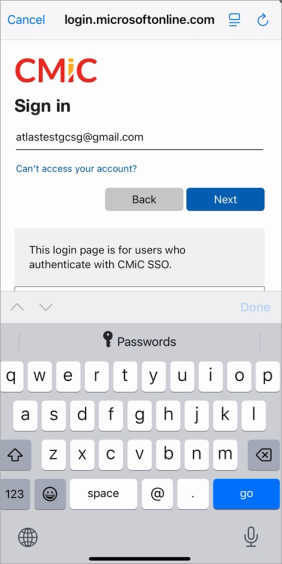
-
You will be redirected to Google to sign in.

-
On the Google Sign in page click [Next] to continue.
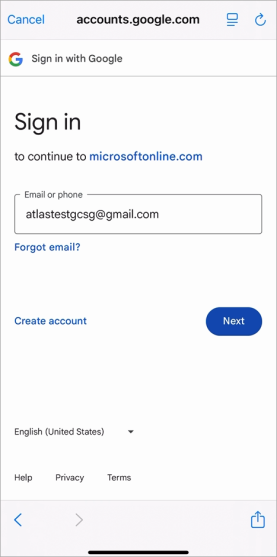
-
Enter your password and click [Next] to continue.
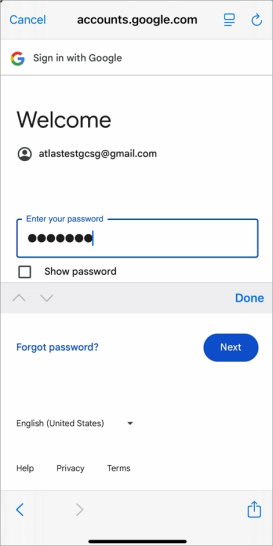
-
Click [Continue] to sign in via OAuth. After entering your credentials,you won't need to authenticate every time you access the app. Instead, you will simply confirm that you wish to proceed with signing in via OAuth, and you will be directed to the project dashboard to enter your project.
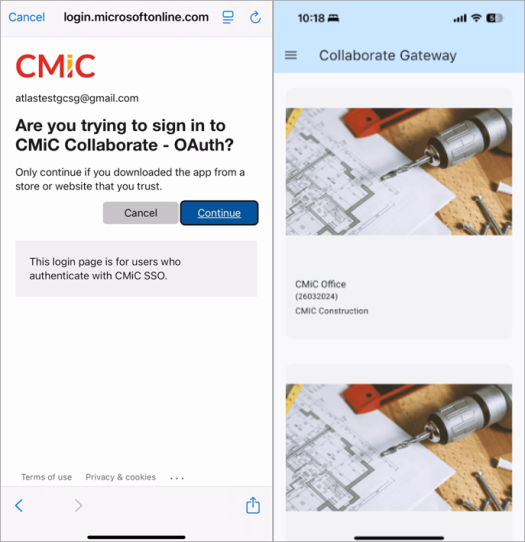
OTP Collaborate Gateway Registration
This is the process flow users can expect when registering with OTP (One-Time Password). In our example, we are using AOL.
-
In the invitation email, click on the [Join Team] button or copy the link into (ideally) private browsing to continue the registration process.
-
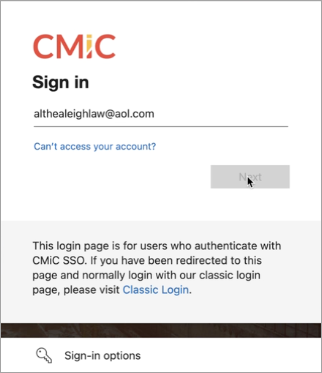
You will be directed to the Microsoft Login page. Enter AOL or other email provider address to sign into your account.
-
A one-time passcode will be sent to your alternate email provider (AOL in this case).
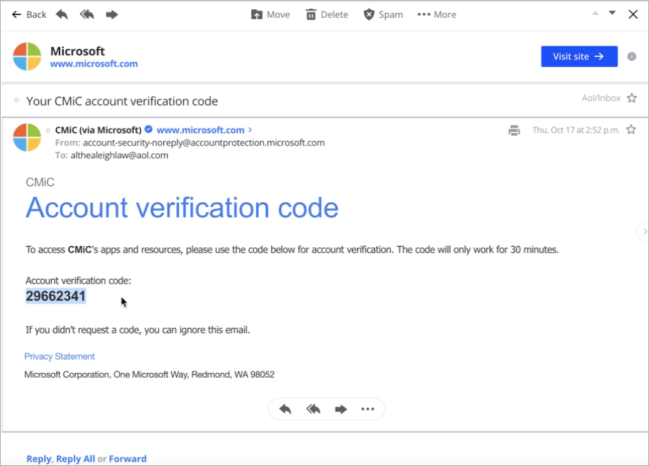
-
Enter your one-time password and press [Sign in].
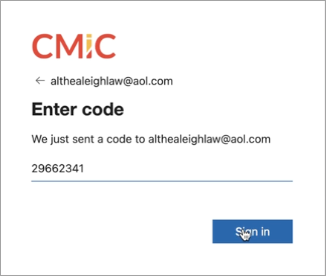
-
You must accept permissions to continue the registration process.
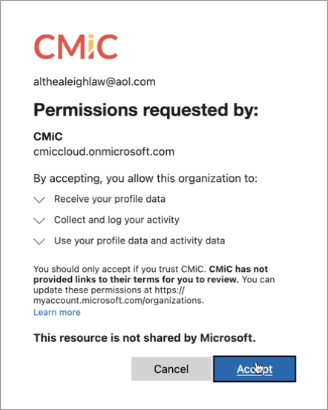
-
You will be prompted to set up multifactor authentication. Press [Next] to continue.
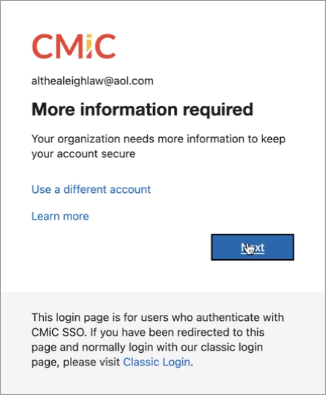
-
Install the Microsoft Authenticator app on your phone. Once the app is installed, press [Next].

-
Continue setting up your account and press [Next].
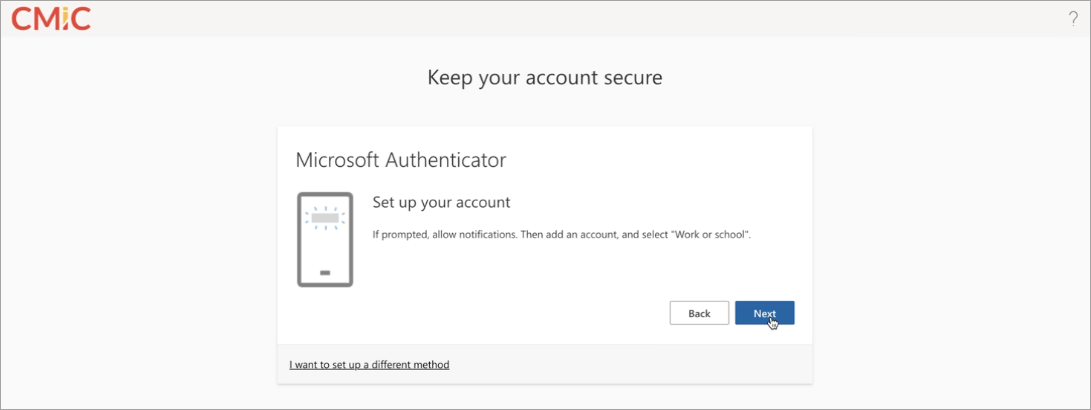
-
Use the Microsoft Authenticator app to scan the QR code. This will connect the Microsoft Authenticator app with your account. After you scan the QR code, press [Next].
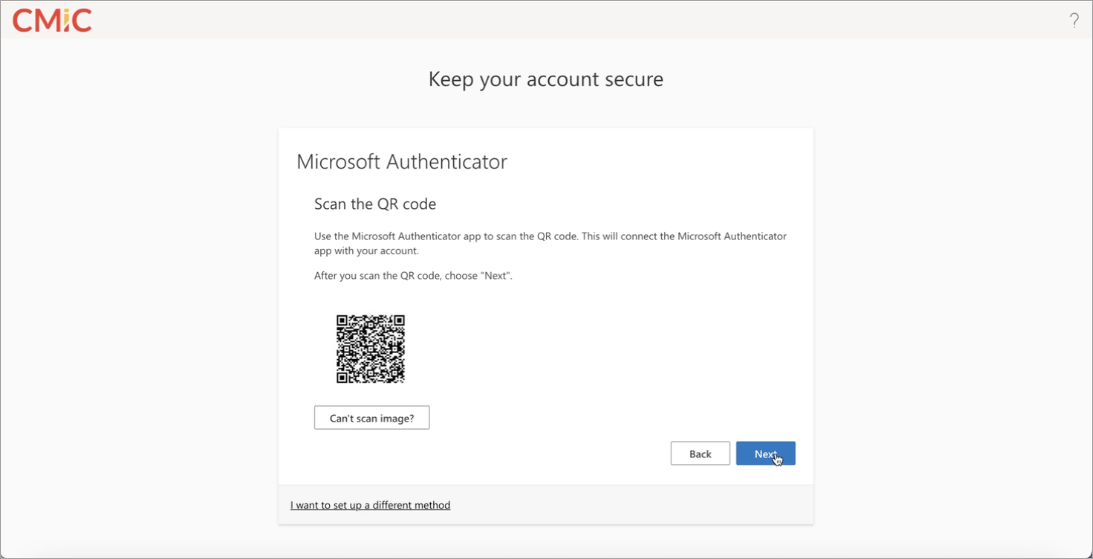
-
Approve the notification being sent to your app by entering the number provided.
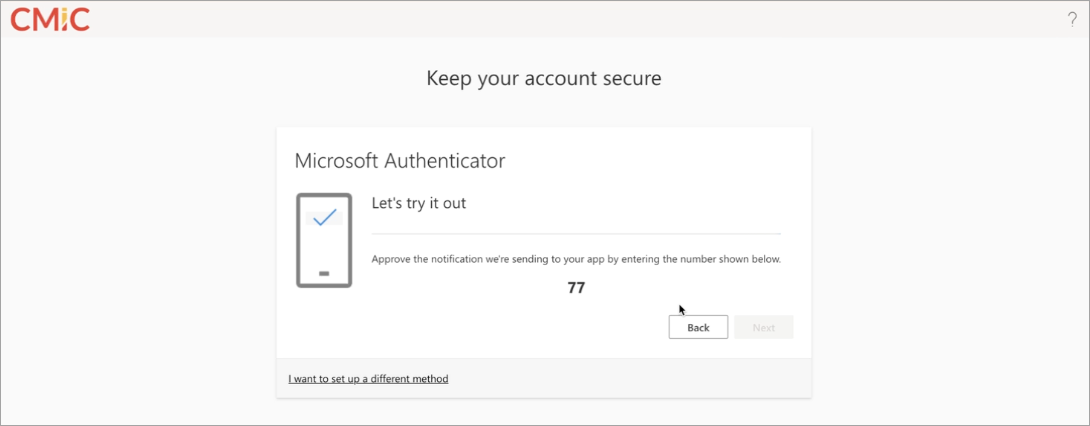
-
Once your Microsoft Authenticator app is successfully registered, press [Done].
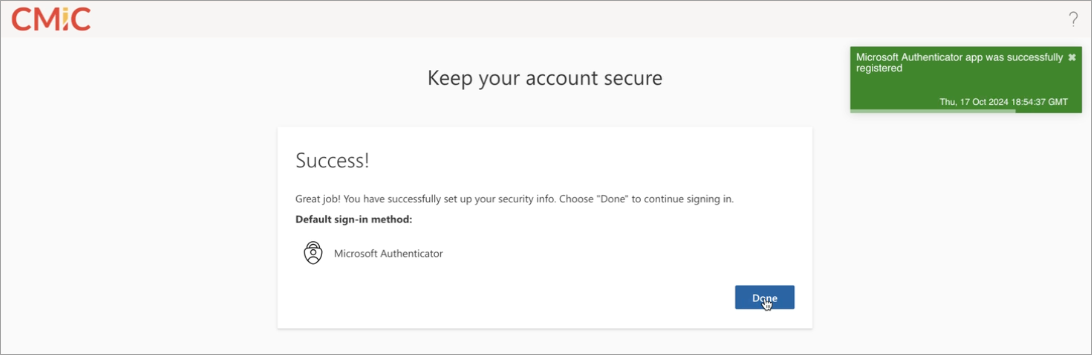
-
Once multifactor authentication has been set up and verified, you will be taken to the project dashboard.
Mobile OTP Collaborate Gateway Login
This is the process flow users can expect when logging in using mobile with OTP (One-Time Password). In our example, we are using AOL.
-
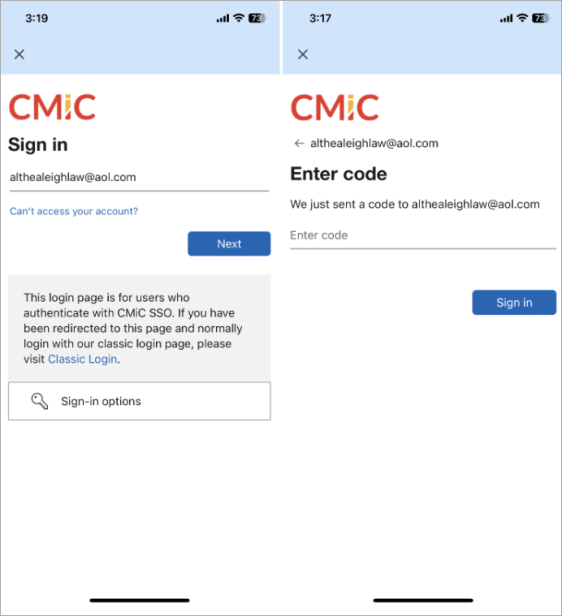
Launch the Construct PM app and tap the [Sign in with Microsoft] button. Sign into your account using your AOL email address or other provider and tap [Next].
-
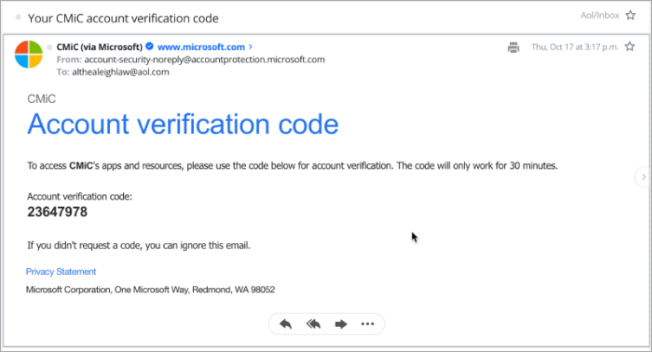
A one-time passcode will be sent to your alternate email provider (AOL in this case).
-
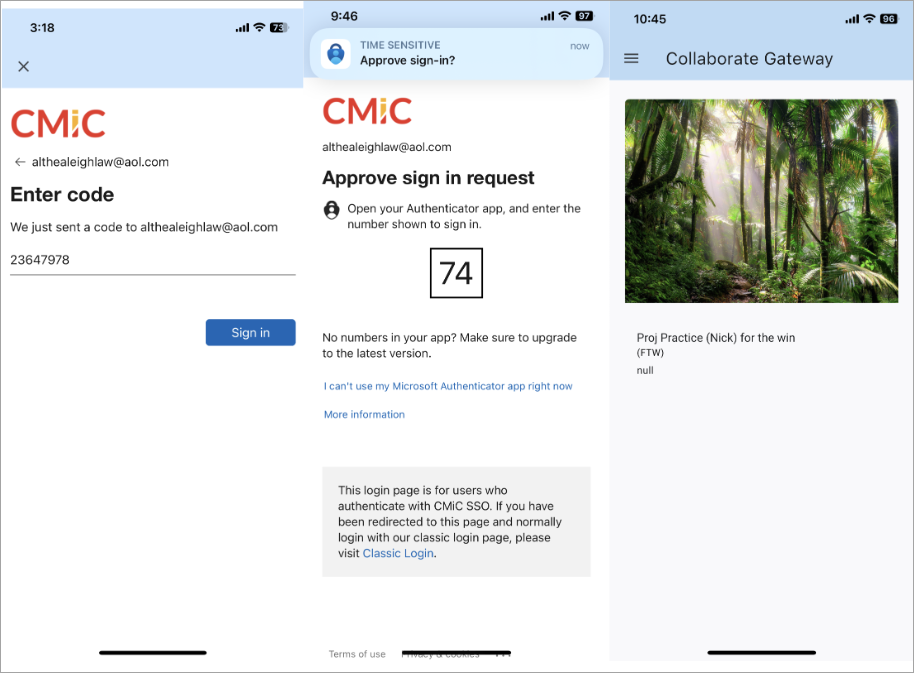
Enter your one-time password and tap [Sign in]. Approve the sign in request by opening your Authenticator app and entering the number shown to sign in. Proceed to Collaborate Gateway.
Collaborate Gateway Login with MFA Off
This is the process flow users can expect when logging in with multifactor authentication (MFA) off.
-
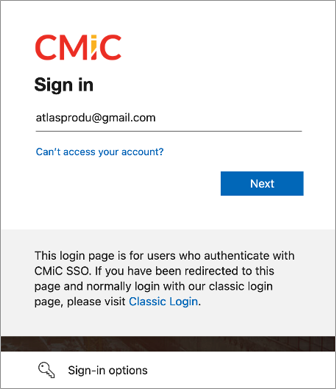
If using https://cmiccollaborate.com/cmictest, you will be redirected to the Microsoft login page. Enter your email address and click [Next].
-
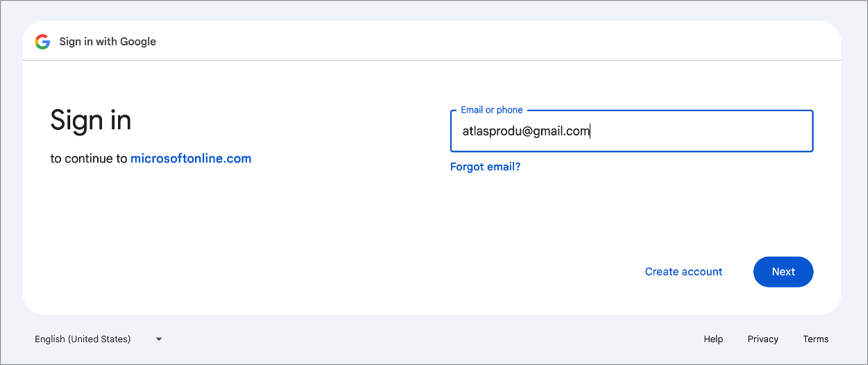
If using a Gmail account, you will be redirected to Gmail. Enter your email address and click [Next].
-
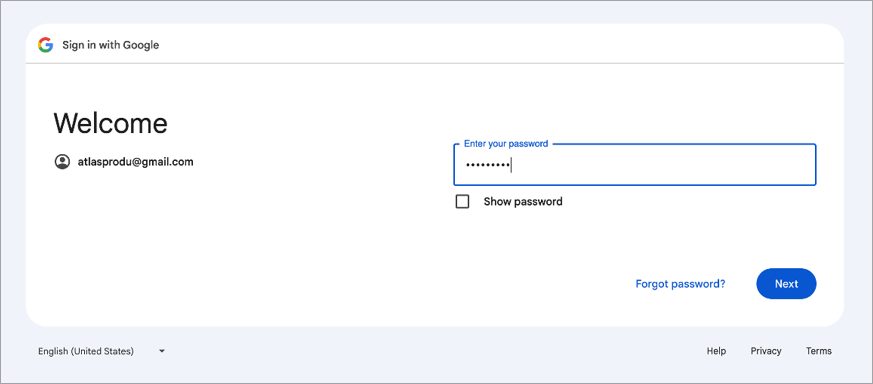
You will be prompted to enter your password. Enter it and click [Next].
-
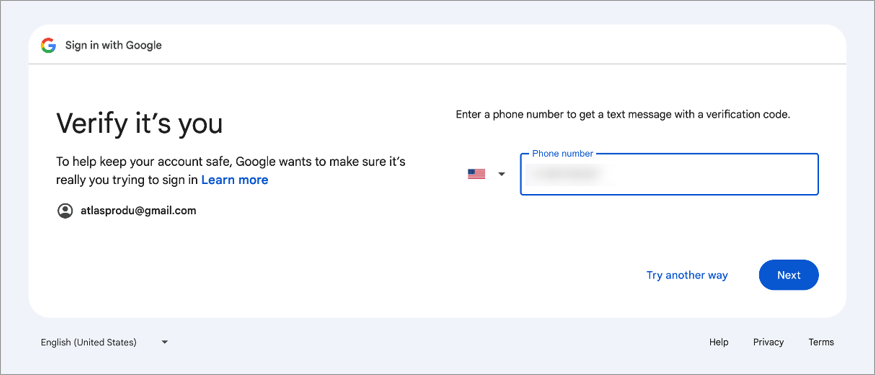
Next you will be prompted to enter a verification method (e.g., phone number). When finished, click [Next].
-
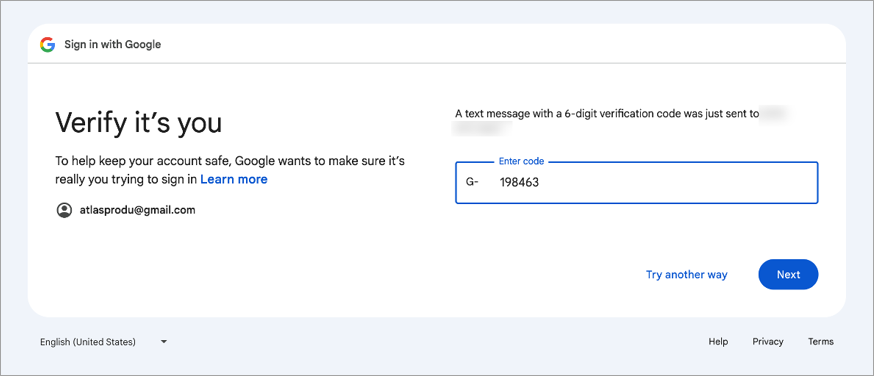
A verification code will be sent based on the method being used and will need to be entered. When finished, click [Next].
-
Once your account has been verified, you will be taken to the project dashboard.
Mobile OTP Collaborate Gateway Login with MFA Off
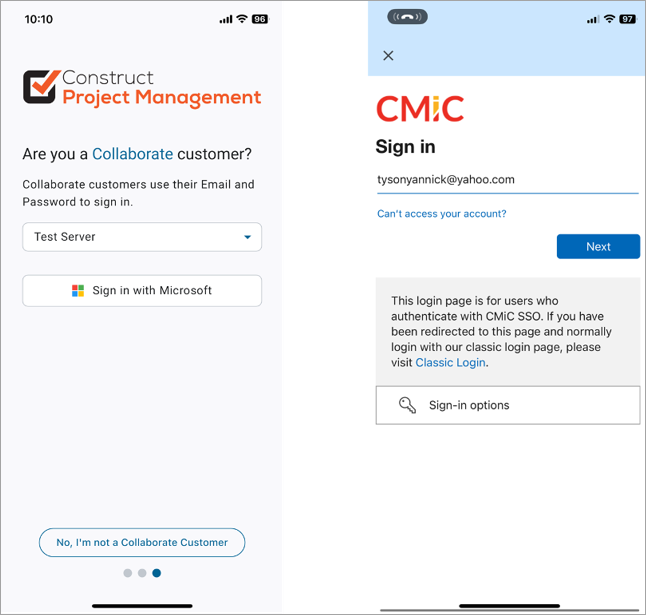
This is the process flow users can expect when logging in using mobile with multifactor authentication (MFA) off using OTP (One-Time Password).
-
Select your server and tap the [Sign In with Microsoft] button. Sign into your account using your email address and tap [Next].
-
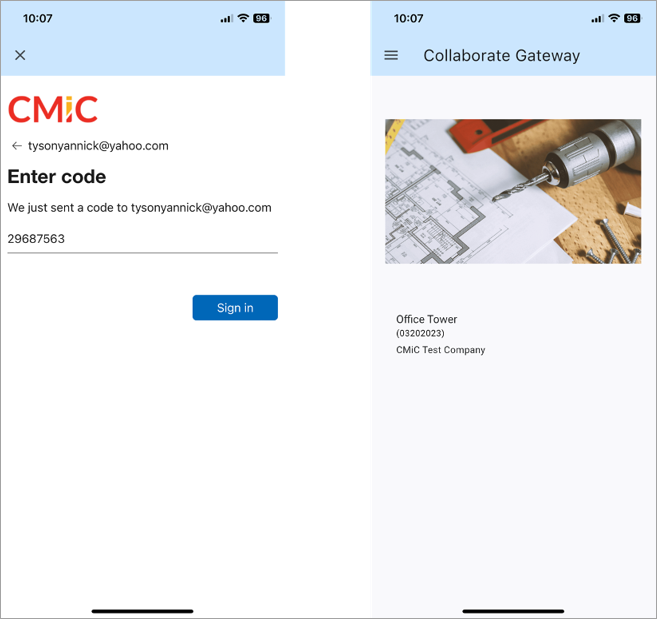
If you are using a non-federated email provider, you will be sent a one-time passcode to enter before being taken to the project dashboard in Collaborate.
FAQ
Do my collaborators need to do anything differently?
No, they will use our web and mobile apps as they do today.
What changes will my collaborators see on their end?
Collaborators will be prompted to enter their email into a different login page. The login page will guide them through to Collaborate Gateway to view their projects. See descriptions for the process flows above.
What if my collaborators don’t use Azure/Microsoft?
We have set up federation with both Azure and Google. If the end user has accounts with neither of these services, we fall back to a one-time passcode that will be sent to their email. This means that collaborators will maintain access to CMiC Collaborate no matter what email/identity provider they are using.
What do I have do to prepare?
Nothing!