CMiC API and OAuth 2.0 Integration - API Security Configuration
This section covers configuring CMiC API Security. API security is based on a role-based access control (RBAC) framework. It is used to grant permissions to your API service account by role, user and specified endpoints.
Step 1: Complete API Program Security Bypass for Other Web Services
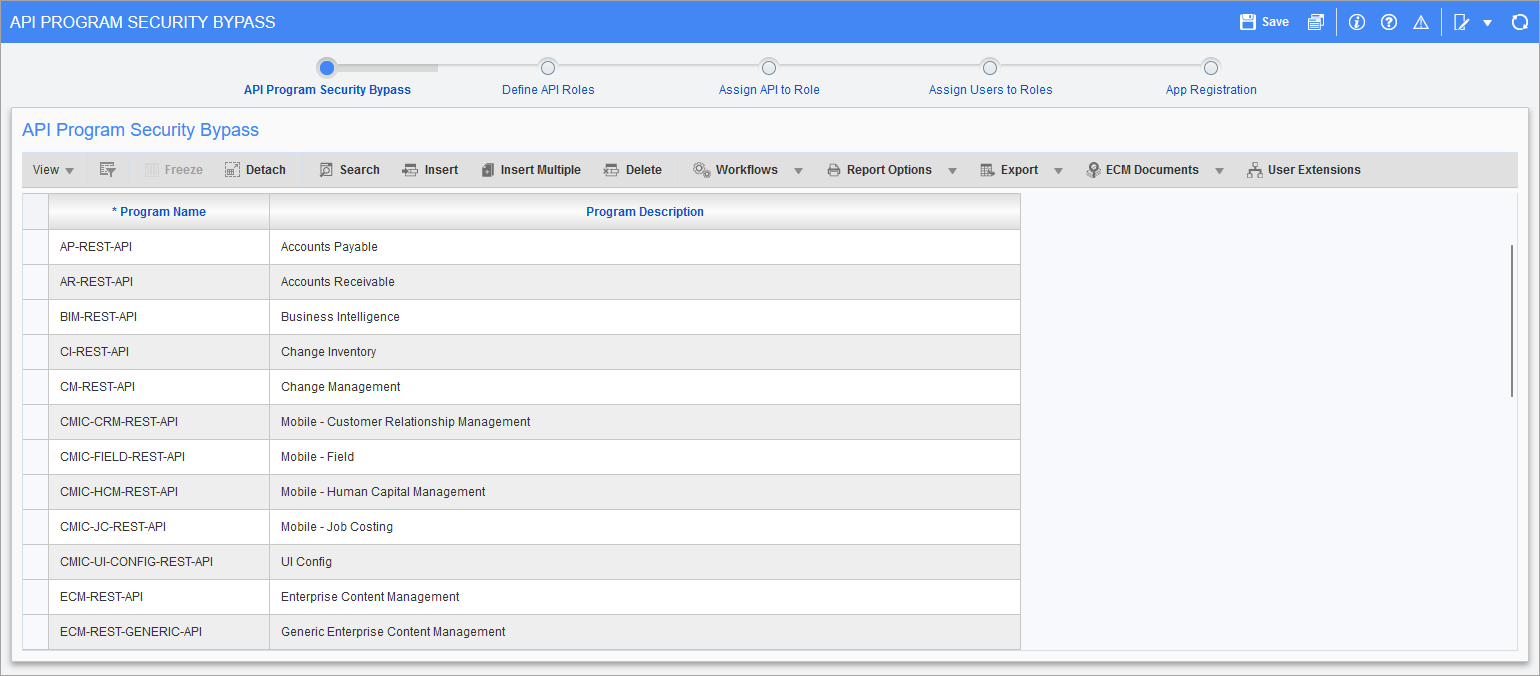
Pgm: SDAPISECBYPAS – API Program Security Bypass; standard Treeview path: System > Security > API Security - API Program Security Bypass
The API Program Security Bypass screen is used for all other web services. This screen lists various program names, and the web services that are housed in these programs will bypass security when it has not been set up. This means that the web service call will go through successfully if the program is listed on this screen.
If security has not been set up, and the program is not listed on this bypass screen, then the web service call will fail with a security message.
Step 2: Define API Roles
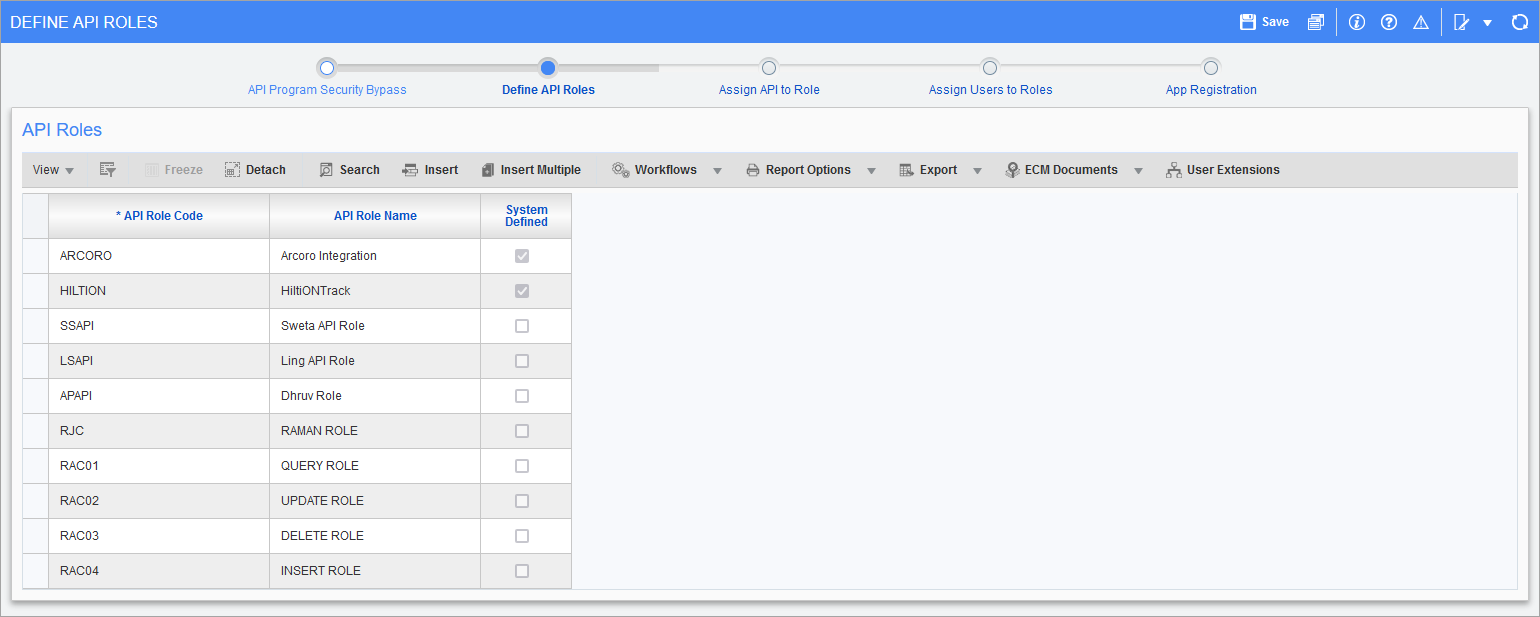
Pgm: SDAPIROLE – API Roles; standard Treeview path: System > Security > API Security - Define API Roles
Follow the process train located at the top of the program and use the Define API Roles screen to create and update your API security roles.
Step 3: Assign API to Role
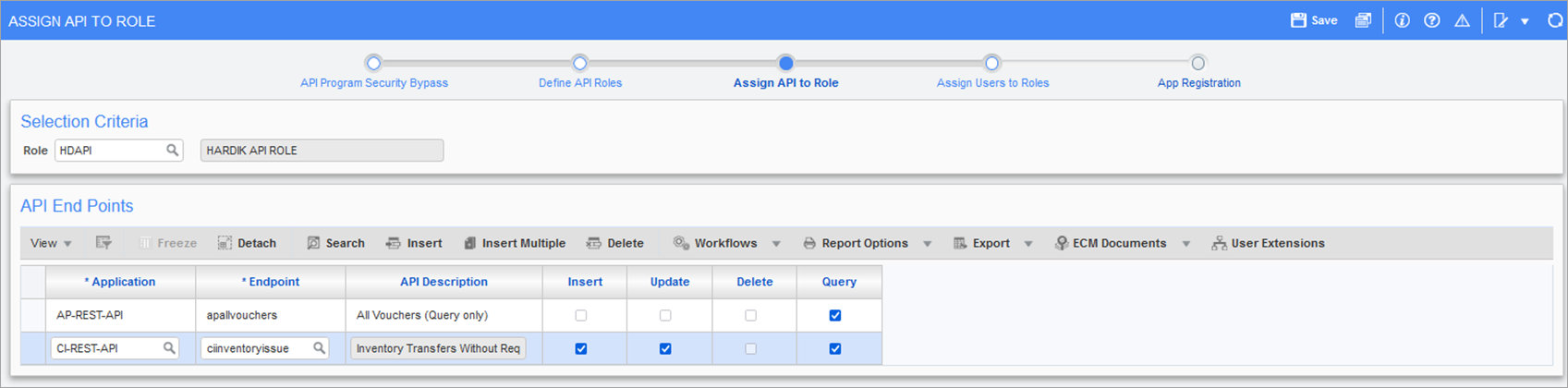
Pgm: SDAPITOROLE – Assign API to Role; standard Treeview path: System > Security > API Security - Assign API to Role
Use the Assign API to Role screen to assign API security role(s) access to available API endpoints (e.g. web services) within an application. Begin by selecting a role code in the Role field, which populates the available endpoints and corresponding actions under the API End Points section.
Click the [Insert] button to add an application to the API End Points section. Proceed to assign an endpoint to the application, and specify any security characteristics (e.g. insert, update, delete, or query) by checking the appropriate boxes.
NOTE: Security is only enabled for the methods (Create, Update, Retrieve or Delete) supported on the selected endpoint, others will be greyed out by default if the method is unavailable.
For the next step only, the setup does differentiate based on if your API/Mobile server has been configured with Basic Authentication versus OAuth2.
If you’d like to configure your APIs with OAuth2, please visit CMiC API and OAuth 2.0 Integration - OAuth 2.0 App Server Setup.
Step 4: Assign Users to Roles for Basic Authentication
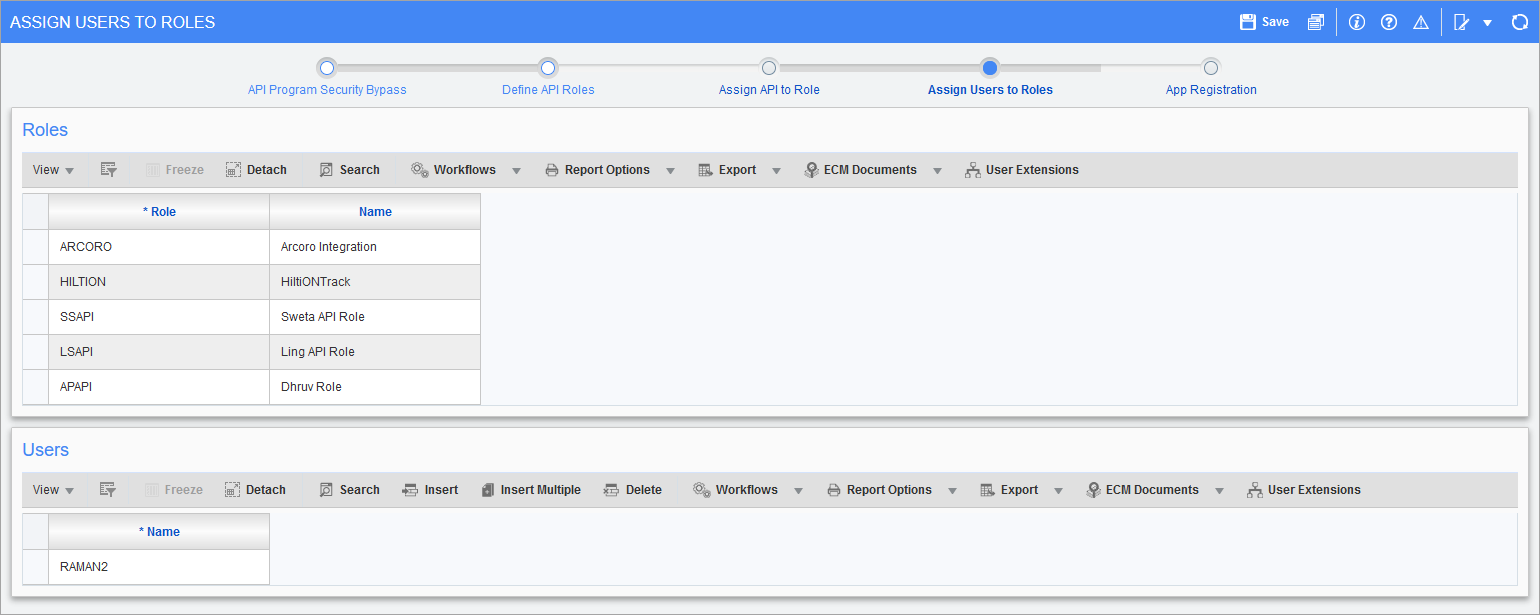
Pgm: SDAPIROLEUSER – Assign Users to Roles; standard Treeview path: System > Security > API Security - Assign Users to Roles
This step applies if your API/Mobile server has been set up to work with Basic Authentication.
Select a role in the Roles section of the screen, then assign users to the selected role using the Users section of the screen. Users can be assigned to any number of roles, and the API security will consider the cumulative setup across all the roles.
Step 5: Register Apps for OAuth2 Authentication
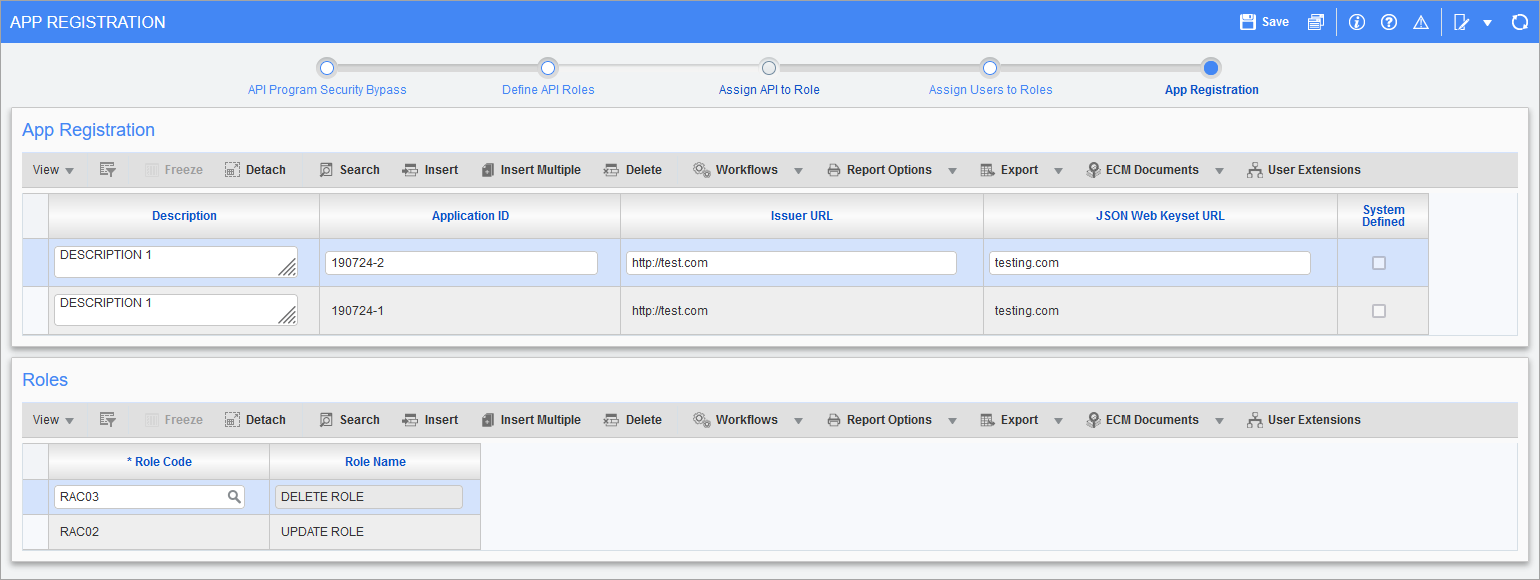
Pgm: SDAPIAPPREG – App Registration; standard Treeview path: System > Security > API Security - App Registration
This step applies if your API/Mobile server has been set up to work with OAuth2.
Use the App Registration screen to register applications using their issuer URL and application ID. These are the fields used in the application security check. Once the application has been registered, they can be assigned corresponding security roles.
Just like their user counterpart, each application can be assigned to any number of roles, and the security will consider the cumulative security set up across all roles.
NOTE: If security has not been set up for a particular user or application, there is a final step in the validation process. Also, if the web service call being made is pointed to the “/describe” resource or “/version” resource. These parameters provide a database introspection into each endpoint that can be called by anyone with access and credentials to the system; no additional security applied.